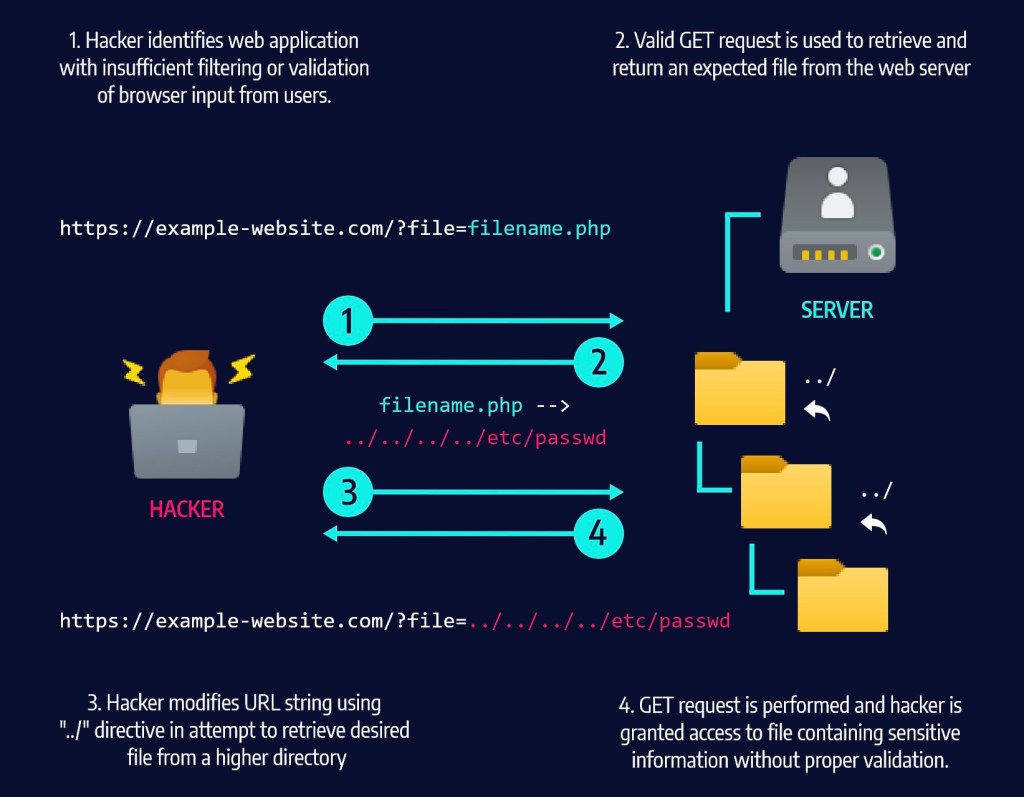
Directory traversal is a type of cyber attack in which an attacker attempts to gain unauthorized access to sensitive files on a server by traversing the server’s directory structure. This type of attack is particularly dangerous because it can allow attackers to gain access to files that are normally inaccessible, such as system and configuration files. The goal of this whitepaper is to detail various methods of mitigating the risk of directory traversal attacks.
One of the most common methods of mitigating the risk of directory traversal attacks is through the use of proper authentication and authorization. By requiring users to authenticate themselves before accessing files, the server can ensure that only authorized users are able to access sensitive information. Additionally, proper authorization rules should be implemented in order to prevent unauthorized users from gaining access to files they do not have permission to view. This can be done by assigning permissions to specific groups and users, thereby limiting the number of individuals who can view certain files.
Furthermore, servers should also utilize access controls specifically designed to prevent directory traversal attacks. For example, web servers should make sure that file requests are within the specified directory structure, and that all requests for files are made through standard HTTP protocols. Additionally, whitelisting specific files and directories can also help to mitigate the risk of directory traversal attacks. This prevents any unknown or malicious file requests from being processed.
Another method of mitigating directory traversal attacks is by implementing secure file deletion techniques. This can include the use of secure erase commands which overwrite files with random data in order to permanently delete them. Additionally, servers should also consider making use of data encryption techniques, which encodes files using complex algorithms and makes them unreadable unless the correct key is used.
Finally, servers should also monitor for attempts to access files outside of their expected directory structure. Detecting suspicious activity can help to identify potential attackers and alert administrators to take action. Moreover, logging requests to specific files can also help to identify malicious actors who are attempting to gain access to restricted information.
By implementing proper authentication and authorization, utilizing access controls, and monitoring for suspicious activity, organizations can better protect themselves against directory traversal attacks.